If you follow technology news, you probably see a lot of headlines about people having their accounts hacked. Just this past August,Twitter CEO Jack Dorsey’s Twitteraccount was hacked. In a short period of time, these hackers posted a series of racist and anti-Semitic tweets on Dorsey’s account. Presumably, they did this in an effort to make him look bad. But fortunately for him, he and his cell carrier were able to publicly clear the air. In light of this kind of news, you might be wondering what kind of chance you stand. After all, if hackers can take advantage of a tech-savvy guy like Jack Dorsey, surely they can hack you.
Thankfully, Dorsey’s account was hacked through a phone carrier exploit, not through his PC. The hackers took advantage of old, unauthenticated cell phone signals to hack his phone. This kind of attack is highly targeted. Hackers aren’t going to use this kind of exploit to hack everyday folks.
A more common method of hacking is to use what’s called a SIM-swapping attack. In this kind of attack, hackers use an old-school method called “social engineering”. Posing as you, they call your cell phone carrier and convince the customer service rep that you need a new SIM. The hackers now have a SIM card in their possession that’s associated with your phone number.
So what in the world does this have to do with internet security? If you use Gmail, Facebook, or most other online services, you’re probably familiar with two factor authentication. This security method requires the use of your phone to reset your password for online services. And in theory, it’s foolproof. Unless someone has SIM-swapped you. In that case, they can instantly gain access to your account. Email accounts are particularly vulnerable to this kind of attack. With your email account, hackers can then gain access to just about any other online account you use. They can gain access to your bank account, your cryptocurrency wallet, and any other sources of your money.

当然,还有其他的攻击有关about. These include ordinary phishing attacks. In a phishing attack, hackers send out a mass email that looks like it comes from a legitimate source. These emails can appear to come from Facebook, your bank, or even a government agency. If you click on a link in the email, you’ll be sent to a phony site that looks like the real thing. Once you’ve entered your login information, the hackers will be able to access your account.
So how do you secure yourself against this kind of attack? One method is to use a two factor authentication USB drive, often called a “security key”. These are compact USB drives that act as a physical key for your account. Even if someone enters the correct username and password, they won’t be able to gain access without the key. Today, we’ll be taking a close look at three of the best security keys on the market. We’ll talk about their features, compatibility, and what you can use them for.
Another physical security option is a fingerprint scanner. These USB devices are similar to security keys. They’re not compatible with as many apps and sites, but they’re even more secure. Only your fingerprint can unlock your device. If this sounds more like what you need, read our review of thebest Windows fingerprint readers. They can lock down any Windows machine, so no-one can use it but you.
How Do Security Keys Work?
如果你一直关注技术more than 10 years, you may be scratching your head. Haven’t security keys been around for a long time? Yes and no. Some varieties have been around since the early 2000s. But these older devices used a method called RSA SecurID. They had a small LCD display attached to a random number generator. Every minute or so, the device would display a new number. There was an identical random number generator on the server side, which would generate an identical number at identical intervals. You’d simply type the number into your login field, and your account would be authenticated.
In 2007, the technology became more sophisticated. Instead of having to type in a random number, you’d just insert the key into your drive. Everything else would happen automatically. However, these security methods still required the random password to be sent back and forth. This left them vulnerable to phishing and man-in-the-middle attacks.

2012年,谷歌与公司合作bico to develop a more secure security key. The end result was a protocol called Universal 2nd Factor (U2F). The companies partnered with PayPal, Lenovo, and others to form the Fast Identity Online (FIDO) Alliance. Their goal was to create a universal protocol that everyone could use. In 2014, the service went live, and was first supported in the Google Chrome browser. Over the next few years, other websites like Facebook, Dropbox, and GitHub also started supporting FIDO U2F. In 2019, the FIDO alliance released the FIDO2 protocol. It’s both more advanced and easier to use, so more companies are expected to add support.
狗U2F通过使用一个JavaScript API调用我们工作b Authentication (WebAuthn). When combined with a security protocol called Client to Administrator Protocol (CTAP), it allows for local authentication. As a result, no vital security data is sent from your computer to the server. Authentication is all performed locally. As a result, this method is theoretically immune to phishing and man-in-the-middle attacks.
Of course, authentication isn’t the be-all and end-all of security. Sometimes, you want to monitor your PC even when you’re not around. There are plenty of apps for this, but a savvy PC user will notice that they’re installed. For more discreet monitoring, consider aUSB keylogger. Not only will they let you know what’s going on, they’re also a great emergency backup for programmers.
Thetis FIDO U2F Security Key
TheThetis FIDO U2F Security Keyis designed to be as durable as possible. It’s designed just like a flip-open thumb drive, with a cover that swings shut to protect the USB connector. But this isn’t just some cheap piece of plastic the manufacturer slapped together to make you feel better. It’s a sturdy anodized aluminum that can take a significant amount of abuse. Thetis is so confident in their product that they’re willing to offer a 12-month warranty against any defects. There’s also a lanyard hole on the back of the cover. This makes it easy to attach the Thetis key to your keychain if you so desire.

Security and Compatibility
The Thetis FIDO U2F key is compatible with any website or app that supports the U2F protocol. This should be expected, given its name. It’s compatible with a wide variety of systems, including Windows, iOS, Linux, and android devices.
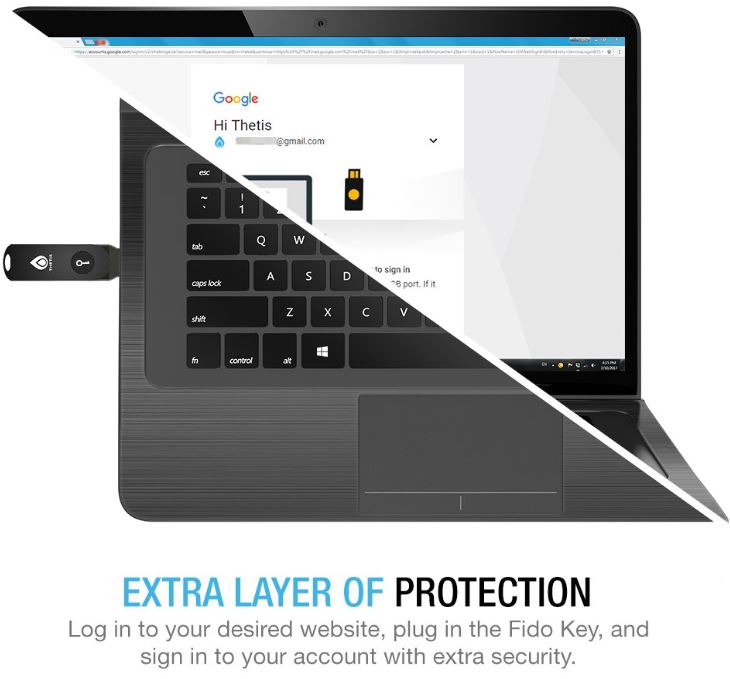
That said, the compatibility is relatively limited. It only supports U2F. Not UAF, OAP, or NFC. As a result, it’s not going to work with anything that doesn’t support U2F. For best results, you’ll want to use it in the Google Chrome browser, since this provides the most compatibility. Be aware that because of these limitations, it’s not compatible with any email clients. If you use Apple Mail, Microsoft Outlook, or Mozilla Thunderbird, you’ll want to choose a security key with more compatibility. On the other hand, the Thetis FIDO U2F Security Key is very reasonably priced. As long as your comfortable with a key that’s limited to Google Chrome, you’re getting excellent security for the price.
Yubico YubiKey 5 NFC
Yubico’sYubiKey 5 NFCis a stylish two factor authentication USB drive that’s designed to carry on your keychain. Like the Thetis key, it’s very well-constructed, with a durable body that’s difficult to damage. It’s made in the USA, which should tell you a thing or two about the overall quality. The USB tip is painted to resemble a circuit board, and it looks like it’s exposed at first glance. Don’t worry. It comes with a silicone cover that protects it from dust, dirt, and water. The cover fits snugly, and stays securely attached even if your fob is dangling from a key ring. That said, it’s not attached in any other way. Be careful not to lose it while the YubiKey 5 is plugged in.

Security and Compatibility
If you’re looking for the absolute most compatibility possible, the YubiKey 5 is tough to beat. Not only does it support FIDO U2F, but it supports the latest FIDO2 protocol that was just released this year. In addition, you’ll have compatibility with many other protocols that are less common. You’ll have support for OATH-TOTP, OATH-HOTP, Smart Card (PIV), and OpenPGP. You’ll also be compatible with Yubico’s OTP protocol, as well as challenge-response capability. Forget about what protocols the YubiKey 5 can use. It would be easier to explain what it can’t use.

The YubiKey 5’s FIDO protocol will allow you to perform just about any function you need within Google Chrome. This is the case on all major operating systems, including Windows, iOS, Android, and most Linux distributions. However, the compatibility with so many protocols allows you to do significantly more. You can use the YubiKey 5 to secure your Gmail, Facebook, Dropbox, and Facebook accounts. It’s also compatible with Microsoft Outlook, so you won’t need to give up your email client.
You’ll also have the ability to use fingerprint authentication. The NFC protocol is supported by Android, iOS, and almost all apps on those platforms.
HyperFIDO Mini
TheHyperFIDO Miniis a compact USB security key that’s designed to take up as little space as possible. It’s only an inch long, barely longer than the USB plug itself. And it ships with a small silicone cover that protects the plug from damage. On the back of the unit, there’s a clear button that you need to press to activate the unit. When it’s turned on, a green LED will illuminate the button, indicating that the HyperFIDO is now active. It also has a pass-through slot for lanyard attachments. However, the pass-through is not very sturdy. Many users report the HyperFido getting pulled off by accident. That said, this security key is very affordably-priced, so you’re getting what you pay for.

Security and Compatibility
The HyperFIDO Mini supports the FIDO U2F protocol, but not the UAF or OTP protocols. Much like the Thetis unit, this limits it to Google Chrome and other FIDO-compatible devices. You can use it with Windows, iOS, or Linux systems. But it’s not compatible with major mail clients and other apps that use non-standard protocols.

The button activation makes the HyperFIDO very secure. If you’re looking for a small key you can plug into the back of your PC, it’s a solid choice. Just tap the button to deactivate it, and no-one will be able to gain access while you’re not around. All in all, that’s an attractive feature on such an affordable device.
Final Verdict
Which one of these security keys is best will vary based on your needs. If you’re looking for physical durability, theThetis FIDO U2F Security Keyis by far your best choice. The aluminum cover is very sturdy, and can handle a lot of abuse. It’s also reasonably-priced, although you’re limited to FIDO-compatible apps.
TheYubico YubiKey 5 NFCis your best choice if you need maximum compatibility. It supports a wide variety of protocols, so you can use major mail clients, as well as a variety of other apps. That said, it’s a bit pricey. If you’re looking for a budget-friendly choice, you might want to look elsewhere.
Finally, theHyperFIDO Miniis the cheapest of the bunch. While the physical construction isn’t the toughest, it’s nonetheless very secure. The push-button toggle makes it ideal if you want a key that stays with your PC. One thing’s for certain. No matter what you’re looking for, at least one of these two factor authentication keys will be ideal for you.







